IT Security Feed
March 5, 2019, 10:23 pm CET
6 years, 6 months ago
[SECURITY] [DSA 4269-1] postgresql-9.6 security update
March 5, 2019, 10:23 pm CET
6 years, 6 months ago
[SECURITY] [DSA 4268-1] openjdk-8 security update
March 5, 2019, 10:23 pm CET
6 years, 6 months ago
[SECURITY] [DSA 4267-1] kamailio security update
March 5, 2019, 10:23 pm CET
6 years, 6 months ago
[CVE-2018-12584] Heap overflow vulnerability in reSIProcate through 1.10.2
March 5, 2019, 10:23 pm CET
6 years, 6 months ago
News, Infocus, Columns, Vulnerabilities, Bugtraq ...
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Nessus Network Monitor Plugin ID 700421 with Medium Severity Synopsis The remote host is running an outdated version of Adobe Flash Player that is affected by multiple attack vectors. Description Versions of Adobe Flash Player prior to 32.0.0.114 are unpatched, and therefore affected by an information disclosure vulnerability. Solution Upgrade to Adobe Flash Player version 32.0.0.114 or later. Read more at ...
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
via www.infosecurity-magazine.com Cybercrime Trends Toward Mobile Bots, Report SaysWhile the volume of mobile bot traffic isn’t anywhere near the volume of traditional desktop bots, new research from ThreatMetrix found that the industry should keep an eye out for mobile bot attacks this year.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
via www.infosecurity-magazine.com No More Stickups, Bank Heists Have Gone CyberModern criminals aren’t taking outrageous risks when it comes to bank robberies, according to a new report. Bank robbers have evolved into cyber-criminals, leverage the digital world to steal from financial institutions in cyberspace.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Comments will be moderated by The Hindu editorial team. Comments that are abusive, personal, incendiary or irrelevant cannot be published. Please write complete sentences. Do not type comments in all capital letters, or in all lower case letters, or using abbreviated text. (example: u cannot substitute for you, d is not 'the', n is not 'and').
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
That includes giving them access to Huawei’s source code — “our crown jewels,” John Suffolk, Huawei’s global cybersecurity and privacy officer told reporters. Suffolk said that while Huawei lets telecom companies use the Brussels centre’s facilities and access its software, it doesn’t necessarily know what they’re doing or searching for.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
An attacker might upload a web shell backdoor to a Joomla Jmail service. A successful exploitation might allow the attacker to run arbitrary code, or use the server as a bot for further attacks.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
RV110W Wireless-N VPN Firewall before 1.2.2.1 RV130W Wireless-N Multifunction VPN Router before 1.0.3.45 RV215W Wireless-N VPN Router before 1.3.1.1 A remote code execution vulnerability exists in Cisco routers management interface. An unauthenticated attacker may use this vulnerability to execute code on the vulnerable server.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Vulnerability Description There exists a directory traversal vulnerability On different web servers. The vulnerability is due to an input validation error in a web server that does not properly sanitize the parameters in request body for the directory traversal patterns.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Experts believe that enterprise-wide data interchange can be streamlined with a dedicated EDI integration software combined with a focused approach. Here are some best practices for supercharging your EDI program. Facebook has undermined privacy on its network by exposing mobile phone numbers....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
BUCHAREST: Romania's biggest opposition party will trigger a public inquiry into Huawei's contribution to critical infrastructure and seek to bar it from 5G network development due to mounting security concerns, its IT expert said on Tuesday. Some Western countries, including the United States and....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
(MENAFN - Newswire.com LLC) SAN FRANCISCO, March 5, 2019 (Newswire.com) - Today marks the start of RSA Conference San Francisco , and the third year in attendance for leading enterprise cyber deception company, CounterCraft . This year CounterCraft is proud to be representing the UK Government's....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Sandeep Baliga, Ethan Bueno de Mesquita, Alexander Wolitzky. Security, Americas If America narrows its focus to China and Russia, then it encourages belligerence by other actors. This increased aggressiveness will create new opportunities in cyberspace for the Chinese and Russians. The Case for a Cyber Deterrence Plan that Works.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Original release date: March 04, 2019. The Internal Revenue Service (IRS) has launched its annual awareness campaign on the 12 most prevalent tax scams, known as the “Dirty Dozen.” As part of the campaign, IRS will highlight one scam each weekday… Original release date: March 04, 2019 The Internal....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
The first outage was mistakenly attributed to a mechanical glitch; after the second, the plant's owners called in investigators. The sleuths found the malware, which has since been dubbed “Triton” (or sometimes “Trisis”) for the Triconex safety controller model that it targeted, which is made by Schneider Electric, a French company.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
, a cybersecurity company purpose built to manage the identity of everything, announced the company is emerging from stealth mode at the Simultaneously, the company released the Armor Platform, a converged hardware token and middleware suite aimed at law enforcement, first responders, government, military, finance, healthcare and transportation.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
These security and risk management trends primarily focus on the security and risk management marketplace (unsurprisingly). However, many of them contextualize the current security information and event management ( SIEM ) marketplace as well. Moreover, these trends may predict future priorities within SIEM solutions.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
to your network. do major damage Using a network performance monitor (NPM) can help you to combat potential – and actual – security risks. While NPMs are designed primarily for use in analyzing network performance, many also have built-in features to help keep track of network security.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
ISACA’s latest State of Cybersecurity Report has found that it’s getting tougher to fill cybersecurity positions, with many organisations waiting three months or longer. 's 2019 State of #Cybersecurity 2019 report was announced today at . Learn more ISACA International (@ISACANews) March 4, 2019....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
, a newsletter that is part of The Washington Post in an attempt to gauge their perspectives on whether critical infrastructure is safer today than it was in 2017 when President Trump signed an executive order (EO) pledging to improve critical infrastructure security.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Better bridges need to be built between IT and operational technology (OT). Focusing on the successes in cybersecurity’s past, Matt Watchinski, vice-president of Cisco Talos , said that “we need to analyze success and failure, as without both sides, we don’t get the full picture.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
RSA While Russian hackers, Kremlin-backed or otherwise, grab the headlines, China remains the biggest cyber-security threat to America, FBI director Christopher Wray warned today. Speaking at the RSA Conference in San Francisco this morning, Wray said the scale of Beijing's government-orchestrated....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Norwich University students joined with Respond Software at the College Football Playoff National Championship at Levi’s Stadium. (Courtesy Respond Software) The College Football Playoff National Championship at Levi’s Stadium on Monday was a winning day for the cybersecurity world monitoring malicious threats at venues.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
SINGAPORE--(BUSINESS WIRE)--Mar 4, 2019-- HackerOne , the leading hacker-powered security platform, Singapore’s (GovTech) and Cyber Security Agency of Singapore (CSA) today announced the successful conclusion of the latest Government Bug Bounty Programme (GBBP), part of the Singapore Government’s....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Spring is (almost) here, which means it’s time for some in-house security cleaning. With the holiday shopping season — one of the most treacherous times of year for security — in the rearview, organizations should take a step back to assess what is working, drop what isn’t and invest in the tools....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
announced Monday it acquired Arlington, Va.-based BluVector , makers of a cybersecurity platform for companies and government agencies, from Philly-based private equity firm LLR Partners. No financial details were released from the sale to Comcast, though two years ago LLR Partners committed $50....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
In IBM's annual X-Force Threat Intelligence Index 2018 , it was determined that “inadvertent insiders” — or employees who accidentally cause security incidents through human error – exposed billions of records between 2015 and 2017. This may help explain why cybercrime keeps getting worse....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
The cyber-security firm eSentire is moving its headquarters from Cambridge to Waterloo. The company will double its floor space in the move to Waterloo's Factory Square, said Rebecca Freiburger, vice-president of corporate communications at eSentire. The plan is to move the company's headquarters this summer.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
In a water scarce country, like South Africa, smart metering can be a utility’s best ally in the fight to preserve water and promote conservation. However as the adoption of Advanced Metering Infrastructure (AMI) becomes more widespread, its appeal to cyber attackers is expected to increase.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
“faster and simpler way for IT security teams to visualise applications and apply security policies in hybrid data centre and cloud environments.” Pavel Gurvich, Co-founder and CEO, Guardicore commented: “The complexities of securing the modern data centre at scale demand effective best practices....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
The Air Force Business Plan , released by the service on Monday, places a strong emphasis on enhancing the Air Force’s IT and cybersecurity capabilities. The plan includes a strong message on the Digital Air Force initiative from Under Secretary Matthew Donovan, who also serves as Chief Management Officer and CIO.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Click to follow The Independent Tech. {{total}} comments Huawei has launched a special "transparency centre" as it attempts to stop people being afraid of it spying on them. The new building in Brussels is an attempt to win back the government leaders and cyber security experts that are worried....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Gernova - Se la priorità del Paese è il lavoro e l’occupazione , sostenere e non subire il rallentamento dell’economia globale, il resto è una conseguenza: è evidente che il lavoro passa attraverso i cantieri e le infrastrutture che non aumentano il debito pubblico.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
NetApp SnapCenter Server prior to 4.0 is susceptible to cross site scripting vulnerability that could allow a privileged user to inject arbitrary scripts into the custom secondary policy label field. Url : http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-15515 CWE : Common Weakness....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
(Reuters) - Diesel USA Inc, the denim and accessory brand known for its jeans, filed for bankruptcy on Tuesday, blaming mounting losses, a sales plunge, expensive leases and cyber fraud. The New York-based unit of Italy's Diesel SpA filed for Chapter 11 protection from creditors with the U.S. bankruptcy court in Delaware.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
The big picture: William Gayde According to the National Security Adviser to House Minority Leader Kevin McCarthy, the NSA has quietly stopped their phone record surveillance program. This program has been extremely controversial since it was famously made public by Edward Snowden but it appears that the Trump Administration has not been using it.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
, Cisco’s technology news site. The Network By 2020, Gartner predicts 20 billion connected devices will be online — and more devices mean more security threats. Connected devices have exploded into the public and corporate landscape, rattling the bars of the cyber security cage.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
There is no "Microsoft Hotmail Update Now". Therefore, Microsoft users who have received the email message below, which claims they won't be able to sign into their email accounts are asked to delete it because it is a phishing scam being sent by cybercriminals to steal Microsoft Windows Live or Outlook usernames and passwords.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Online users, beware of fake "DHL Shipment Notification" emails like the one below. The fake emails have links that go to fake DHL websites once they have clicked. If visitors to the fake website attempt to sign into the fake DHL website with their account credentials, they will be redirected to legitimate DHL website at www.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
SAN FRANCISCO. Christopher Krebs today made his first RSA conference presentation as head of DHS’ Cybersecurity and Infrastructure Security Agency – last year he was still leading the old NPPD – and said four priorities are guiding his work: Chinese threats to the telecom supply chain, securing....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Introduction sur SEMrush. SEMrush est une plateforme qui permet de faire énormément de choses, à tel point qu’on peut rapidement s’y perdre. Pour vous donner une idée de l’architecture du service, il faut savoir que SEMRush permet de suivre des campagnes de référencement sur le long terme via ce....
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
INDUSTRY INSIGHT Government data security is a no-brainer with the cloud By Mark Rohrbach; Mar 05, 2019. Already in 2019 there have been several large data breaches, each resulting in the exposure of significant volumes of sensitive information and identities.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
There are plenty of reasons for organizations to embrace edge computing. By moving applications, data, and computing services to the edge of a network, as opposed to a large data center or cloud, organizations can lower operating costs, improve application performance, reduce network traffic, and achieve real-time data analytics.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
KUALA LUMPUR: Malaysian budget carrier AirAsia Group said it was launching a venture capital fund in the United States to invest in startups seeking to enter or expand in Southeast Asia. The fund, called RedBeat Capital, will focus on post-seed-stage startups in travel and lifestyle, financial technology, artificial intelligence and cybersecurity.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
The first exchange traded fund to invest in 5G - the next generation of wireless technology - launched Tuesday. The new ETF, launched by a company that manages funds for disruptive technologies, invests in equipment, mobile network operators, real estate businesses, and other components of 5G networks.
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
RSA Microsoft has wheeled out two new enterprise security tools – Azure Sentinel, a cloud-based SIEM, and Microsoft Threat Experts, an infosec advice-as-a-service bundled with a panic button. The two services are part of Redmond's ongoing invasion of the cloud security market .
March 5, 2019, 10:21 pm CET
6 years, 6 months ago
Kiinalainen päätelaite- ja verkkolaitevalmistaja Huawei avaa tiistaina EU:n ytimessä Brysselissä keskuksen, johon se kutsuu jäsenmaiden viranomaisia tarkistamaan verkkolaitteidensa ohjelmakoodia ja tietoturvaa – myös Suomesta. Useissa maissa hallitukset tekevät tietoturvaan liittyviä päätöksiä vain....
March 5, 2019, 10:17 pm CET
6 years, 6 months ago
[SECURITY] [DSA 4269-1] postgresql-9.6 security update
March 5, 2019, 10:17 pm CET
6 years, 6 months ago
[SECURITY] [DSA 4268-1] openjdk-8 security update
March 5, 2019, 10:17 pm CET
6 years, 6 months ago
[SECURITY] [DSA 4267-1] kamailio security update
March 5, 2019, 10:17 pm CET
6 years, 6 months ago
[CVE-2018-12584] Heap overflow vulnerability in reSIProcate through 1.10.2
March 5, 2019, 10:17 pm CET
6 years, 6 months ago
News, Infocus, Columns, Vulnerabilities, Bugtraq ...
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Nessus Network Monitor Plugin ID 700421 with Medium Severity Synopsis The remote host is running an outdated version of Adobe Flash Player that is affected by multiple attack vectors. Description Versions of Adobe Flash Player prior to 32.0.0.114 are unpatched, and therefore affected by an information disclosure vulnerability. Solution Upgrade to Adobe Flash Player version 32.0.0.114 or later. Read more at ...
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
There is no "Microsoft Hotmail Update Now". Therefore, Microsoft users who have received the email message below, which claims they won't be able to sign into their email accounts are asked to delete it because it is a phishing scam being sent by cybercriminals to steal Microsoft Windows Live or Outlook usernames and passwords.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Online users, beware of fake "DHL Shipment Notification" emails like the one below. The fake emails have links that go to fake DHL websites once they have clicked. If visitors to the fake website attempt to sign into the fake DHL website with their account credentials, they will be redirected to legitimate DHL website at www.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
The big picture: William Gayde According to the National Security Adviser to House Minority Leader Kevin McCarthy, the NSA has quietly stopped their phone record surveillance program. This program has been extremely controversial since it was famously made public by Edward Snowden but it appears that the Trump Administration has not been using it.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Original release date: March 04, 2019. The Internal Revenue Service (IRS) has launched its annual awareness campaign on the 12 most prevalent tax scams, known as the “Dirty Dozen.” As part of the campaign, IRS will highlight one scam each weekday… Original release date: March 04, 2019 The Internal....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
The first outage was mistakenly attributed to a mechanical glitch; after the second, the plant's owners called in investigators. The sleuths found the malware, which has since been dubbed “Triton” (or sometimes “Trisis”) for the Triconex safety controller model that it targeted, which is made by Schneider Electric, a French company.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
, a cybersecurity company purpose built to manage the identity of everything, announced the company is emerging from stealth mode at the Simultaneously, the company released the Armor Platform, a converged hardware token and middleware suite aimed at law enforcement, first responders, government, military, finance, healthcare and transportation.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
These security and risk management trends primarily focus on the security and risk management marketplace (unsurprisingly). However, many of them contextualize the current security information and event management ( SIEM ) marketplace as well. Moreover, these trends may predict future priorities within SIEM solutions.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
to your network. do major damage Using a network performance monitor (NPM) can help you to combat potential – and actual – security risks. While NPMs are designed primarily for use in analyzing network performance, many also have built-in features to help keep track of network security.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Better bridges need to be built between IT and operational technology (OT). Focusing on the successes in cybersecurity’s past, Matt Watchinski, vice-president of Cisco Talos , said that “we need to analyze success and failure, as without both sides, we don’t get the full picture.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
RSA While Russian hackers, Kremlin-backed or otherwise, grab the headlines, China remains the biggest cyber-security threat to America, FBI director Christopher Wray warned today. Speaking at the RSA Conference in San Francisco this morning, Wray said the scale of Beijing's government-orchestrated....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Comments will be moderated by The Hindu editorial team. Comments that are abusive, personal, incendiary or irrelevant cannot be published. Please write complete sentences. Do not type comments in all capital letters, or in all lower case letters, or using abbreviated text. (example: u cannot substitute for you, d is not 'the', n is not 'and').
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
That includes giving them access to Huawei’s source code — “our crown jewels,” John Suffolk, Huawei’s global cybersecurity and privacy officer told reporters. Suffolk said that while Huawei lets telecom companies use the Brussels centre’s facilities and access its software, it doesn’t necessarily know what they’re doing or searching for.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Kiinalainen päätelaite- ja verkkolaitevalmistaja Huawei avaa tiistaina EU:n ytimessä Brysselissä keskuksen, johon se kutsuu jäsenmaiden viranomaisia tarkistamaan verkkolaitteidensa ohjelmakoodia ja tietoturvaa – myös Suomesta. Useissa maissa hallitukset tekevät tietoturvaan liittyviä päätöksiä vain....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
BUCHAREST: Romania's biggest opposition party will trigger a public inquiry into Huawei's contribution to critical infrastructure and seek to bar it from 5G network development due to mounting security concerns, its IT expert said on Tuesday. Some Western countries, including the United States and....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
via www.infosecurity-magazine.com Cybercrime Trends Toward Mobile Bots, Report SaysWhile the volume of mobile bot traffic isn’t anywhere near the volume of traditional desktop bots, new research from ThreatMetrix found that the industry should keep an eye out for mobile bot attacks this year.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
NetApp SnapCenter Server prior to 4.0 is susceptible to cross site scripting vulnerability that could allow a privileged user to inject arbitrary scripts into the custom secondary policy label field. Url : http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-15515 CWE : Common Weakness....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
(Reuters) - Diesel USA Inc, the denim and accessory brand known for its jeans, filed for bankruptcy on Tuesday, blaming mounting losses, a sales plunge, expensive leases and cyber fraud. The New York-based unit of Italy's Diesel SpA filed for Chapter 11 protection from creditors with the U.S. bankruptcy court in Delaware.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Gernova - Se la priorità del Paese è il lavoro e l’occupazione , sostenere e non subire il rallentamento dell’economia globale, il resto è una conseguenza: è evidente che il lavoro passa attraverso i cantieri e le infrastrutture che non aumentano il debito pubblico.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
The cyber-security firm eSentire is moving its headquarters from Cambridge to Waterloo. The company will double its floor space in the move to Waterloo's Factory Square, said Rebecca Freiburger, vice-president of corporate communications at eSentire. The plan is to move the company's headquarters this summer.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Vulnerability Description There exists a directory traversal vulnerability On different web servers. The vulnerability is due to an input validation error in a web server that does not properly sanitize the parameters in request body for the directory traversal patterns.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Experts believe that enterprise-wide data interchange can be streamlined with a dedicated EDI integration software combined with a focused approach. Here are some best practices for supercharging your EDI program. Facebook has undermined privacy on its network by exposing mobile phone numbers....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
An attacker might upload a web shell backdoor to a Joomla Jmail service. A successful exploitation might allow the attacker to run arbitrary code, or use the server as a bot for further attacks.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
RV110W Wireless-N VPN Firewall before 1.2.2.1 RV130W Wireless-N Multifunction VPN Router before 1.0.3.45 RV215W Wireless-N VPN Router before 1.3.1.1 A remote code execution vulnerability exists in Cisco routers management interface. An unauthenticated attacker may use this vulnerability to execute code on the vulnerable server.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
ISACA’s latest State of Cybersecurity Report has found that it’s getting tougher to fill cybersecurity positions, with many organisations waiting three months or longer. 's 2019 State of #Cybersecurity 2019 report was announced today at . Learn more ISACA International (@ISACANews) March 4, 2019....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
, a newsletter that is part of The Washington Post in an attempt to gauge their perspectives on whether critical infrastructure is safer today than it was in 2017 when President Trump signed an executive order (EO) pledging to improve critical infrastructure security.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
announced Monday it acquired Arlington, Va.-based BluVector , makers of a cybersecurity platform for companies and government agencies, from Philly-based private equity firm LLR Partners. No financial details were released from the sale to Comcast, though two years ago LLR Partners committed $50....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Click to follow The Independent Tech. {{total}} comments Huawei has launched a special "transparency centre" as it attempts to stop people being afraid of it spying on them. The new building in Brussels is an attempt to win back the government leaders and cyber security experts that are worried....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
(MENAFN - Newswire.com LLC) SAN FRANCISCO, March 5, 2019 (Newswire.com) - Today marks the start of RSA Conference San Francisco , and the third year in attendance for leading enterprise cyber deception company, CounterCraft . This year CounterCraft is proud to be representing the UK Government's....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Sandeep Baliga, Ethan Bueno de Mesquita, Alexander Wolitzky. Security, Americas If America narrows its focus to China and Russia, then it encourages belligerence by other actors. This increased aggressiveness will create new opportunities in cyberspace for the Chinese and Russians. The Case for a Cyber Deterrence Plan that Works.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
via www.infosecurity-magazine.com No More Stickups, Bank Heists Have Gone CyberModern criminals aren’t taking outrageous risks when it comes to bank robberies, according to a new report. Bank robbers have evolved into cyber-criminals, leverage the digital world to steal from financial institutions in cyberspace.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
In a water scarce country, like South Africa, smart metering can be a utility’s best ally in the fight to preserve water and promote conservation. However as the adoption of Advanced Metering Infrastructure (AMI) becomes more widespread, its appeal to cyber attackers is expected to increase.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
The Air Force Business Plan , released by the service on Monday, places a strong emphasis on enhancing the Air Force’s IT and cybersecurity capabilities. The plan includes a strong message on the Digital Air Force initiative from Under Secretary Matthew Donovan, who also serves as Chief Management Officer and CIO.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Spring is (almost) here, which means it’s time for some in-house security cleaning. With the holiday shopping season — one of the most treacherous times of year for security — in the rearview, organizations should take a step back to assess what is working, drop what isn’t and invest in the tools....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
Norwich University students joined with Respond Software at the College Football Playoff National Championship at Levi’s Stadium. (Courtesy Respond Software) The College Football Playoff National Championship at Levi’s Stadium on Monday was a winning day for the cybersecurity world monitoring malicious threats at venues.
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
In IBM's annual X-Force Threat Intelligence Index 2018 , it was determined that “inadvertent insiders” — or employees who accidentally cause security incidents through human error – exposed billions of records between 2015 and 2017. This may help explain why cybercrime keeps getting worse....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
“faster and simpler way for IT security teams to visualise applications and apply security policies in hybrid data centre and cloud environments.” Pavel Gurvich, Co-founder and CEO, Guardicore commented: “The complexities of securing the modern data centre at scale demand effective best practices....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
SINGAPORE--(BUSINESS WIRE)--Mar 4, 2019-- HackerOne , the leading hacker-powered security platform, Singapore’s (GovTech) and Cyber Security Agency of Singapore (CSA) today announced the successful conclusion of the latest Government Bug Bounty Programme (GBBP), part of the Singapore Government’s....
March 5, 2019, 10:16 pm CET
6 years, 6 months ago
, Cisco’s technology news site. The Network By 2020, Gartner predicts 20 billion connected devices will be online — and more devices mean more security threats. Connected devices have exploded into the public and corporate landscape, rattling the bars of the cyber security cage.
March 5, 2019, 10:13 pm CET
6 years, 6 months ago
RSA announced at the RSA Conference new enhancements to its award-winning Integrated Risk Management platform, RSA Archer, to help customers fundamentally transform their risk management function. As organizations rapidly evolve and embrace digital technologies to provide their organizations a competitive advantage, new forms of risk are created. Due to the connected nature of the modern enterprise, these digital risks challenge the status quo for risk and cybersecurity teams, third-party ...
March 5, 2019, 10:10 pm CET
6 years, 6 months ago
Written by Mar 5, 2019 | CYBERSCOOP. Sean Lyngaas A year ago, cybersecurity researchers at Trend Micro who were tinkering with home-automation systems in their spare time decided to make a formal project out of it. One of the researchers invited the others to hack his smart home in Germany and see....
March 5, 2019, 10:09 pm CET
6 years, 6 months ago
RSA Conference 2019 is underway at the Moscone Center in San Francisco. Check out our microsite for the conference for all the most important news. Here are a few photos from the Expo floor. Featured vendors include: Anomali, ObserveIT, ZeroFOX, Corero Network Security, Aruba, CenturyLink, Sumo Logic, Fasoo, and Netscout. The post Photo gallery: RSA Conference 2018 Expo appeared first on Help Net Security .
March 5, 2019, 10:02 pm CET
6 years, 6 months ago
One of the things I find most interesting about Abovitz is that he’s never worked for anyone else, other than his board of directors. He did odd jobs as a kid. He worked for his dad. He had an internship, but never a boss. Mako’s rise to a public company, and its subsequent acquisition by Stryker Surgical for $1.
March 5, 2019, 10:02 pm CET
6 years, 6 months ago
Tweet This ForbesWomen But what does a woman-forward internet look like? For some, it starts with building greater protections for users. There’s an old maxim in fiction: Write what you know. And the best writers — those who are able to create authentic and effective worlds — draw from their own experiences.
Feed : News@Cisco: Latest Security News
URL : https://newsroom.cisco.com/data/syndication/rss2/news_at_cisco_5Security.xml
Cisco Elevates the SOC with Agentic AI for Faster Threat Response and Reduced Complexity
02:00 PM Tuesday, September 9, 2025
Splunk Enterprise Security Premier Edition and Essentials Edition advance unified threat detection and response
More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.html
Cisco Supercharges Observability with Agentic AI for Real-Time Business Insights
02:00 PM Tuesday, September 9, 2025
Splunk Observability unlocks actionable AI insights to help organizations improve the reliability of their entire digital estate
More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.html
AT&T and Cisco Deliver Comprehensive Secure Access Service Edge (SASE) Solution
02:00 PM Wednesday, August 27, 2025
AT&T SASE with Cisco combines AT&T's network expertise with Cisco's advanced security and networking technologies.
More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.html
Are you ready for some football? Cisco triples NFL franchise and stadium partnerships ahead of 2025-2026 season
04:00 PM Tuesday, August 26, 2025
As the new NFL season kicks off, Cisco is proud to be playing an even bigger role in one of the world’s most iconic sports leagues.
More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.html
Cisco Delivers Critical AI Infrastructure for Top NFL Franchises
04:00 PM Tuesday, August 26, 2025
Expands use of Cisco's industry-leading enterprise networking and cybersecurity solutions to six additional NFL franchises venues
More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.html
Research insights: 4 trends reshaping identity security in 2025
02:00 PM Tuesday, August 26, 2025
As security threats surge in the AI era, Duo and Cisco Identity Intelligence help security leaders overcome hurdles to adopt key identity-security measures.
More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.html
Talking network visibility, operational efficiency, and cybersecurity with Jorge Ramirez
02:00 PM Monday, August 18, 2025
GM’s Jorge Ramirez discusses network segmentation, security, and other ways GM utilizes Cisco tech in its plants worldwide.
More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.html
Cisco Reports Fourth Quarter Earnings
10:05 PM Wednesday, August 13, 2025
Cisco reported fourth quarter revenue of $14.7 billion, net income on a generally accepted accounting principles (GAAP) basis of $2.8 billion or $0.71 per share, and non-GAAP net income of $4.0 billion or $0.99 per share.
More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.html
ReVault! When your SoC turns against you…
02:00 PM Tuesday, August 5, 2025
Cisco Talos recommends actions to mitigate attack scenarios involving the compromise of a ControlVault device.
More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.html
At Cisco, bold steps towards a quantum network
02:00 PM Friday, August 1, 2025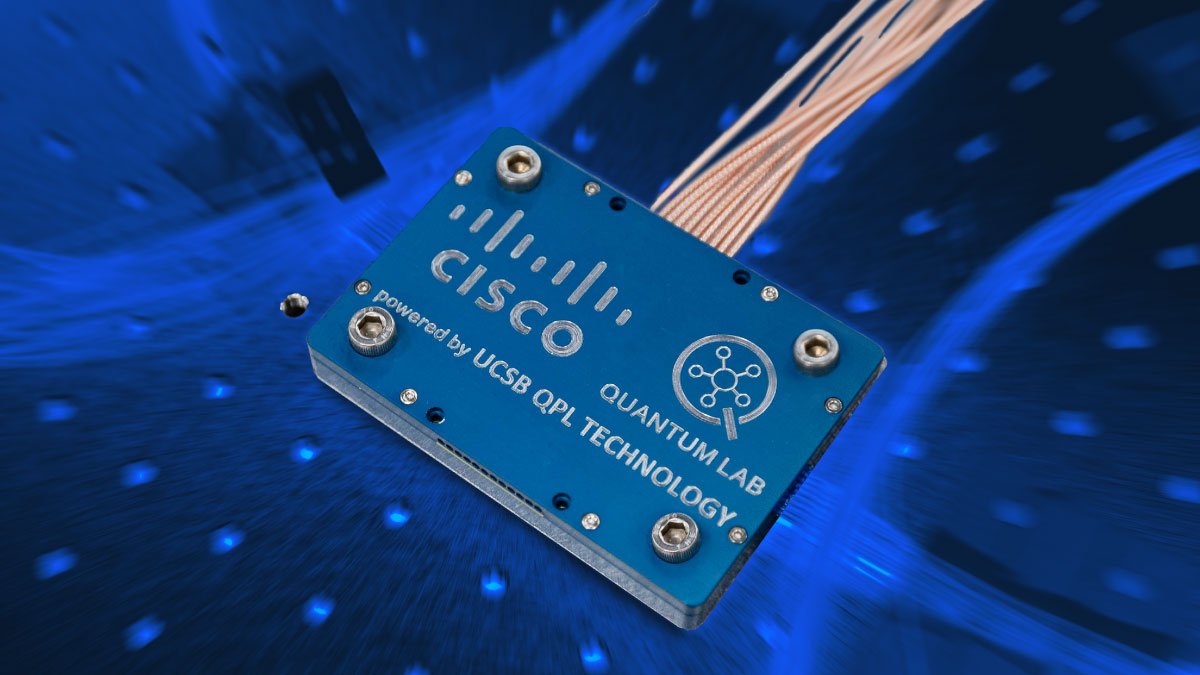
With its foundational quantum innovations, Cisco spurs a tech revolution that could help solve pressing global and industry problems.
More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.html

